Quantum Leap: Quantum computing is no longer just science fiction-it’s a fast-approaching technological leap that will transform the way we protect our digital world. In this article, we’ll explore what quantum computing is, why it matters for cybersecurity, and what steps individuals and organizations should take to prepare for this new era.
Whether you’re a curious student, a tech enthusiast, or a cybersecurity professional, this guide will help you understand the risks, opportunities, and practical actions needed to stay secure in the quantum age.
Table of Contents
Quantum Leap
| Topic | Key Data & Stats | Professional Insights |
|---|---|---|
| Quantum Computing & Cybersecurity | 67% of experts expect increased cyber risks from quantum computing | Quantum-safe skills are in high demand; PQC and QKD are growth areas |
| Encryption Threat | RSA/ECC encryption could be broken within 5-15 years | Urgent need for migration to post-quantum cryptography |
| Industry Readiness | Only 33% of firms feel prepared for quantum risks | Cybersecurity professionals with quantum expertise will lead future innovation |
| Career Opportunities | PQC, quantum risk management, and QKD are emerging fields | Masters in cybersecurity with quantum focus is highly valuable |
Quantum computing is set to revolutionize both the threats and defenses in cybersecurity. While the timeline for quantum threats remains uncertain, the risks are too significant to ignore. By staying informed, planning ahead, and investing in quantum-safe technologies and skills, individuals and organizations can turn this quantum leap into an opportunity for stronger, more resilient digital security. The future of cybersecurity will be shaped by how well we prepare today for the quantum challenges of tomorrow.
What Is Quantum Computing?
Quantum computing is a new type of computer technology that uses the strange rules of quantum physics. Unlike traditional computers, which use bits (0s and 1s), quantum computers use qubits-which can be both 0 and 1 at the same time. This unique property, known as superposition, allows quantum computers to process a vast number of possibilities simultaneously.
Another important quantum property is entanglement, where qubits become linked so that the state of one instantly influences the state of another, no matter how far apart they are. These quantum effects give quantum computers the potential to solve certain problems much faster than even the most powerful supercomputers today.
Why Is Quantum Computing Important for Cybersecurity?
Most of the world’s digital security relies on mathematical problems that are hard for classical computers to solve. For example, when you send a secure message or make an online payment, encryption algorithms like RSA or ECC protect your information. These algorithms are safe today because it would take regular computers thousands of years to break them.
Quantum computers, however, could solve these problems in hours or even minutes. This means that once quantum computers are powerful enough, they could break the encryption that keeps our data safe. This potential has profound implications for everything from personal privacy to national security.
How Quantum Computing Threatens Cybersecurity
1. Breaking Modern Encryption
- RSA and ECC Vulnerability: Quantum computers running algorithms like Shor’s algorithm could easily break RSA and ECC encryption, which protect everything from banking to government secrets. These algorithms rely on the difficulty of factoring large numbers or solving discrete logarithms-tasks quantum computers can handle efficiently.

- “Harvest Now, Decrypt Later” Attacks: Hackers may already be collecting encrypted data, planning to decrypt it once quantum computers are available. This means sensitive information such as medical records, intellectual property, and classified government communications could be at risk even before quantum computers become mainstream.
2. Impact on Businesses and Critical Infrastructure
- Business Disruption: Many experts believe quantum computing could disrupt business models, especially those relying on secure digital transactions, such as e-commerce, banking, and cloud services. The loss of trust in digital security could have wide-reaching economic consequences.
- Critical Infrastructure Risks: Utilities, healthcare, transportation, and government systems rely heavily on secure communications and data protection. A breach caused by quantum-enabled attacks could lead to service outages, data theft, or even sabotage.
3. Timeline for Quantum Threats

- When Will It Happen? Experts estimate that a “cryptographically relevant quantum computer” (CRQC) capable of breaking current encryption could arrive within 5 to 15 years. However, this timeline is uncertain and depends on technological breakthroughs. Because of this uncertainty, experts recommend early preparation to avoid being caught off guard.
How Quantum Computing Can Improve Cybersecurity
Quantum computing isn’t just a threat-it also brings new tools for defense and innovation in cybersecurity.
1. Quantum-Safe Cryptography (Post-Quantum Cryptography, PQC)
- What Is PQC? PQC refers to new encryption methods designed to withstand attacks from both classical and quantum computers. These algorithms rely on mathematical problems believed to be resistant to quantum attacks, such as lattice-based cryptography and hash-based signatures.
- Adoption and Testing: PQC algorithms are currently being standardized and tested by cybersecurity experts and major technology companies. Transitioning to PQC is a critical step to future-proof digital security.
2. Quantum Key Distribution (QKD)
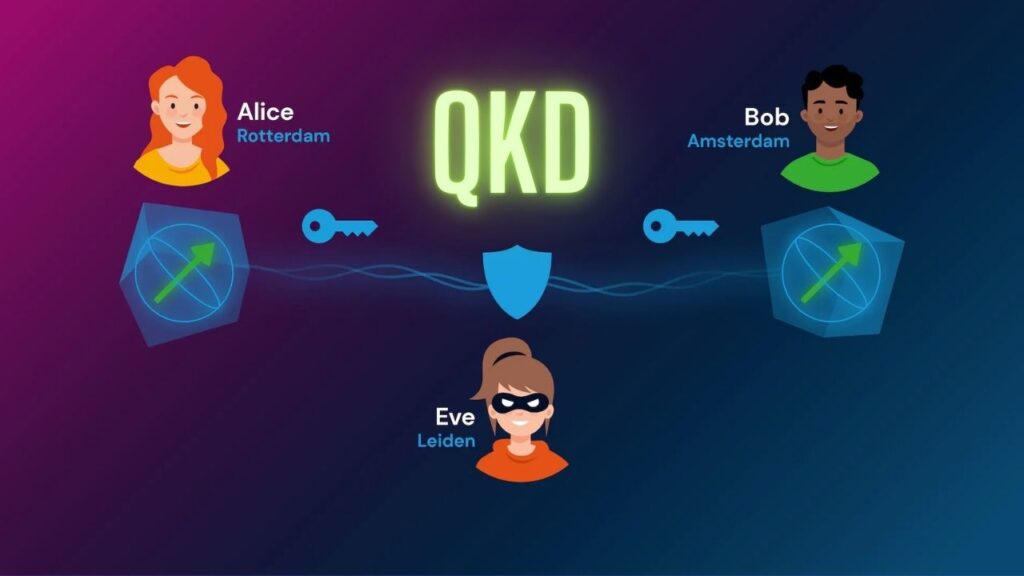
- Ultra-Secure Communications: QKD uses the principles of quantum mechanics to generate and share encryption keys securely. Any attempt to intercept or measure the quantum key changes its state, alerting the communicating parties to the presence of an eavesdropper. This method offers theoretically unbreakable security.
- Practical Use Cases: While QKD currently works best over short distances or specialized fiber optic networks, ongoing research aims to extend its reach, potentially enabling a global quantum-secure internet.
3. Faster Threat Detection

- Big Data Analysis: Quantum computers could process and analyze enormous datasets much faster than classical computers. This capability could revolutionize cybersecurity by enabling real-time detection of complex cyberattacks, advanced persistent threats, and anomalies that are difficult to spot today.
Practical Steps for Individuals and Organizations
Preparing for the quantum cybersecurity era requires proactive efforts. Here’s a clear, step-by-step guide to help you get started:
1. Stay Informed
- Keep up with the latest developments in quantum computing and cybersecurity through trusted news sources, industry reports, and professional organizations.
- Join webinars, workshops, and forums focused on quantum-safe security.
2. Assess Your Risk
- Conduct an inventory of your digital assets and identify which systems rely on vulnerable encryption.
- Understand the sensitivity and longevity of your data-information that needs to remain confidential for many years is especially at risk.
3. Plan for Migration
- Develop a roadmap to transition to quantum-safe cryptographic algorithms.
- Work with vendors and IT teams to ensure that software and hardware can support new encryption standards as they become available.
4. Invest in Skills and Training
- For cybersecurity professionals, gaining knowledge in quantum computing fundamentals and post-quantum cryptography is increasingly valuable.
- Organizations should provide training to IT and security teams to build internal expertise.
5. Collaborate and Share Knowledge
- Engage with industry groups, government agencies, and academic institutions to stay ahead of emerging threats and best practices.
- Sharing threat intelligence and collaborating on standards will strengthen the overall security ecosystem.
Real-World Examples
- Google: Google has been a pioneer in testing post-quantum cryptography, integrating quantum-safe algorithms into its internal communications to evaluate their performance and security.
- Apple: Apple has introduced post-quantum cryptographic protocols in its messaging platforms to enhance user privacy against future quantum threats.
- IBM: IBM offers quantum-safe toolkits and consulting services to help organizations prepare for the quantum transition and secure their data against emerging risks.
Inside the Lab: Breakthroughs in Organic Solar Cells Could Change Energy Forever
From Silicon to Organic Semiconductors: The Future of Computing Explained
10 Emerging Materials Set to Transform Electronics in the Next Decade
FAQs About Quantum Leap
Q1: How soon will quantum computers break today’s encryption?
Most experts believe this could happen within 5 to 15 years, but the timeline is uncertain. Because data stolen today can be stored and decrypted later, it’s important to start preparing now.
Q2: What is post-quantum cryptography (PQC)?
PQC is a set of new encryption methods designed to resist attacks from both classical and quantum computers, ensuring long-term data security.
Q3: What should businesses do to prepare?
Businesses should assess their current encryption, develop migration plans to quantum-safe algorithms, and train their cybersecurity teams on emerging quantum risks.
Q4: Will quantum computers make all cybersecurity obsolete?
No. While quantum computers threaten current encryption methods, new quantum-safe technologies and strategies are being developed to protect data and communications.
Q5: Are there career opportunities in quantum cybersecurity?
Yes! As quantum computing grows, demand for experts in quantum-safe cryptography, quantum risk management, and quantum key distribution is increasing rapidly.