NIST Releases Finalized Post-Quantum Cryptography Standards: As quantum computing technology rapidly advances, the need to secure our digital infrastructure against the unique threats it poses has never been greater. On August 13, 2024, the National Institute of Standards and Technology (NIST) officially published the first set of finalized post-quantum cryptography (PQC) standards, marking a milestone in global cybersecurity efforts.

These standards define new cryptographic algorithms designed to resist attacks from quantum computers — machines capable of breaking the widely-used encryption methods that currently protect sensitive data worldwide. Understanding these standards, their significance, and how to prepare for the quantum era is critical for organizations, governments, and technology professionals.
Why Post-Quantum Cryptography Standards Are Essential
Today’s digital security largely depends on public-key cryptography, with RSA and elliptic curve cryptography (ECC) being the most popular algorithms used to secure everything from emails and bank transactions to cloud data and national defense communications.
However, quantum computers, by exploiting principles of quantum mechanics, threaten to render these cryptosystems obsolete. In particular, Shor’s algorithm, developed in 1994, can factor large numbers exponentially faster than classical algorithms, effectively breaking RSA and ECC encryption in seconds when scaled quantum hardware becomes available.
This is not just theoretical; organizations around the world are racing to develop practical quantum computers. Once operational at scale, quantum machines will endanger current encryption, exposing private data and critical infrastructure to cyberattacks.
What Is Post-Quantum Cryptography?
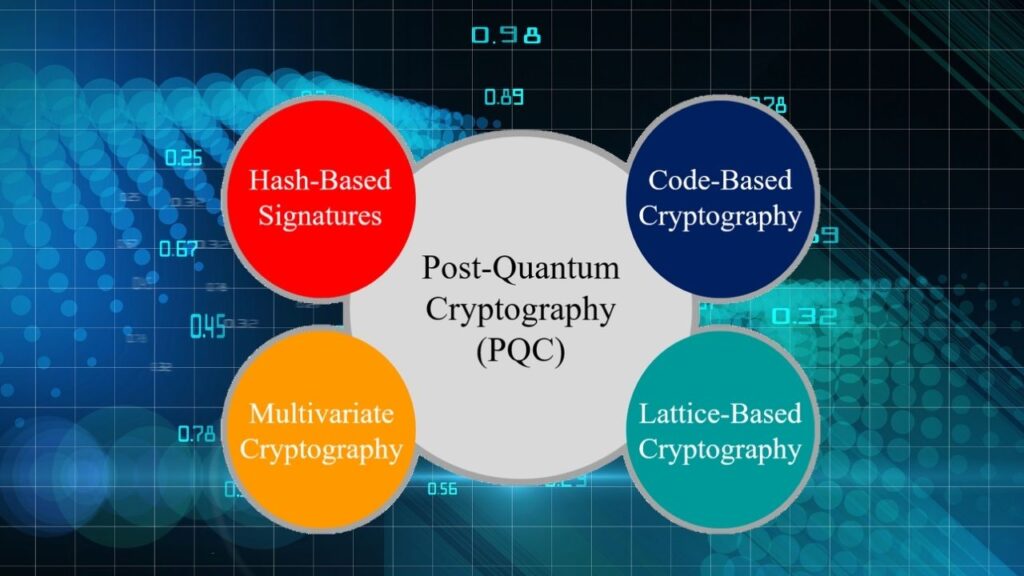
Post-Quantum Cryptography (PQC) refers to cryptographic algorithms designed to be secure against both classical and quantum computer attacks. Unlike quantum cryptography, which relies on quantum communication methods, PQC uses classical computing techniques but is constructed on mathematical problems believed to be hard for quantum computers to solve.
Examples of such problems include lattice-based cryptography, hash-based signatures, code-based cryptography, and multivariate polynomial cryptography.
The primary goals of PQC are:
- Resist quantum attacks — even from powerful quantum computers in the future.
- Maintain efficiency — algorithms should be practical for real-world applications with acceptable speed and key sizes.
- Be interoperable — algorithms must integrate smoothly with existing protocols and systems.
NIST’s PQC Standardization Journey
NIST launched the PQC standardization project in 2016 to evaluate and select quantum-resistant public-key cryptographic algorithms. The project invited submissions from researchers worldwide, evaluating 69 algorithms through multiple rounds based on security, performance, and implementation feasibility.
By July 2022, NIST announced a shortlist of four algorithms selected for standardization, followed by an ongoing review of backup options.
After rigorous testing and refinement, on August 13, 2024, NIST published the finalized standards:
| Standard | Algorithm Basis | Purpose | Notes |
|---|---|---|---|
| FIPS 203 | CRYSTALS-Kyber | Key Encapsulation Mechanism (KEM) | High performance and small key sizes |
| FIPS 204 | CRYSTALS-Dilithium | Digital Signature Algorithm (DSA) | Efficient signatures, moderate key sizes |
| FIPS 205 | SPHINCS+ | Stateless Hash-Based Digital Signature | Backup scheme, highly conservative |
The release of the first finalized post-quantum cryptography standards by NIST is a pivotal advancement in protecting our digital future. Quantum computing is no longer science fiction but an approaching reality with the power to break current cryptographic systems.
By adopting these quantum-resistant algorithms early, organizations will safeguard sensitive information, maintain trust, and future-proof their systems against emerging cyber threats.
The road ahead involves planning, testing, and collaboration — but the time to start is now. Prepare to embrace the quantum-secure era and ensure your data’s confidentiality and integrity for decades to come.
A fourth algorithm, HQC (Hamming Quasi-Cyclic), remains under review with a draft standard expected by 2026 and final publication in 2027.
Detailed Breakdown of the Finalized Algorithms
1. CRYSTALS-Kyber (FIPS 203)

- What It Is: A lattice-based key encapsulation mechanism that facilitates secure exchange of encryption keys over insecure channels.
- Why It Matters: Kyber offers excellent performance with comparatively small key sizes, making it well-suited for constrained environments like Internet of Things (IoT) devices and mobile networks.
- Technical Strengths: Resistant to known quantum attacks, Kyber uses structured lattices for both speed and security. It fits well into existing protocols like TLS 1.3.
- Use Cases: Secure web browsing, VPN connections, encrypted messaging apps.
2. CRYSTALS-Dilithium (FIPS 204)
- What It Is: A digital signature scheme based on lattice problems, used to verify authenticity and integrity of data.
- Why It Matters: Dilithium balances security, efficiency, and simplicity, making it practical for software updates, secure emails, and document signing.
- Technical Strengths: Produces signatures with moderate size and computational requirements, fitting many applications’ needs.
- Use Cases: Code signing, identity verification, blockchain technologies.
3. SPHINCS+ (FIPS 205)
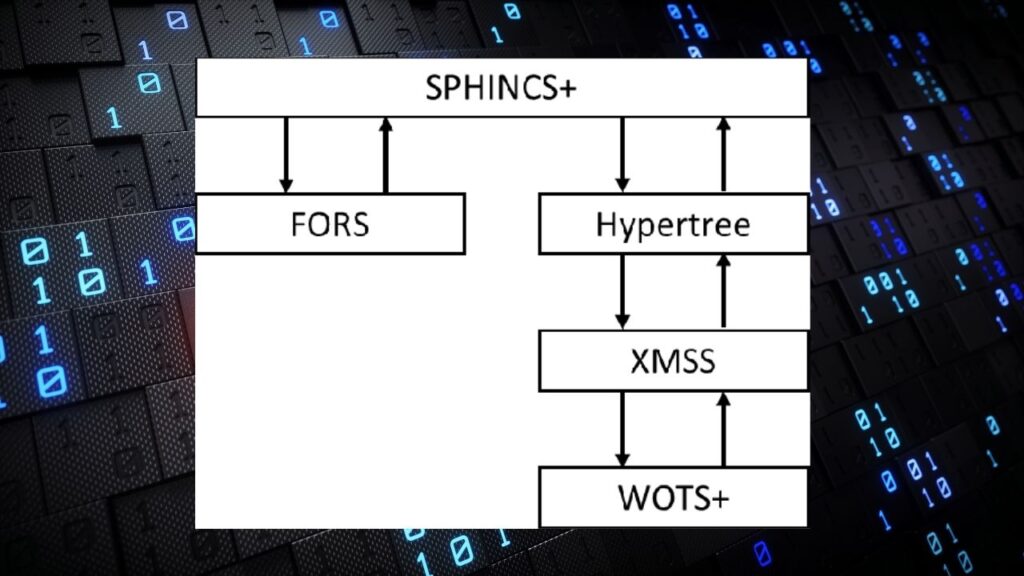
- What It Is: A stateless, hash-based digital signature scheme that acts as a conservative backup.
- Why It Matters: It does not rely on lattice assumptions and instead uses well-understood hash functions, providing a different cryptographic foundation.
- Technical Strengths: Highly secure and resistant to quantum attacks but relatively large signatures and slower performance compared to lattice schemes.
- Use Cases: Firmware signing, long-term secure archival signatures.
How NIST’s Standards Affect You and Your Organization
Impact Across Industries
Post-quantum cryptography standards will impact a wide range of sectors including:
- Government: Protecting classified communications and critical infrastructure.
- Finance: Securing online banking, transactions, and financial data.
- Healthcare: Safeguarding patient data and medical records.
- Telecommunications: Ensuring secure voice, messaging, and network infrastructure.
- Cloud Computing: Protecting cloud storage and services accessed globally.
- Internet of Things (IoT): Securing billions of connected devices with constrained resources.
What Organizations Should Do Now
- Inventory and Assess: Identify systems using vulnerable cryptography, particularly RSA and ECC.
- Plan Transition Strategies: Develop a roadmap for adopting PQC algorithms. Hybrid solutions that combine classical and PQC algorithms are recommended during transition periods.
- Test and Validate: Evaluate PQC implementations in test environments. Participate in pilot projects or collaborate with vendors.
- Update Policies and Compliance: Align cybersecurity policies with upcoming mandates and standards.
- Train Staff: Ensure your cybersecurity teams are educated on PQC technologies and deployment challenges.
Implementing PQC: Practical Considerations and Challenges
Key Size and Performance Trade-offs
PQC algorithms generally have larger keys or signatures compared to traditional RSA/ECC. For example:
- Kyber’s public keys are larger than RSA but smaller than some other PQC candidates.
- SPHINCS+ signatures can be hundreds of kilobytes, impacting bandwidth.
Organizations must balance security with resource constraints, especially on embedded devices.
Integration with Existing Protocols
Protocols like TLS, SSH, and VPN must be updated to support PQC algorithms. Many implementations are already underway, with hybrid cryptographic suites allowing incremental upgrades.
Long-Term Security
One major concern is “harvest now, decrypt later” attacks, where adversaries record encrypted data now to decrypt it later once quantum computers become capable. Transitioning sooner to PQC reduces this risk.
Global Alignment and Regulatory Landscape
NIST’s PQC standards serve as a foundation for many countries’ cybersecurity strategies. International standards bodies like ISO/IEC JTC 1 SC 27 are evaluating these algorithms for global adoption.
In the United States, a White House directive mandates federal agencies to migrate to PQC by 2035, with initial assessments starting in 2025. Private sectors in critical infrastructure and finance face increasing regulatory pressure to prepare.
NSF Announces New Funding for NextG Wireless Research
Hong Kong Showcases 20 Start-ups at VivaTech 2025: A Deep Dive into Innovation and Global Ambitions
FAQs About NIST Releases Finalized Post-Quantum Cryptography Standards
What makes an algorithm “quantum-resistant”?
It relies on mathematical problems that quantum computers cannot efficiently solve, such as lattice-based or hash-based constructions.
Will PQC replace all current encryption?
Eventually, but the transition will be gradual with hybrid models initially.
Is PQC only for governments?
No, organizations of all sizes handling sensitive data should plan for PQC.
How soon should businesses act?
Start now — inventory systems, test PQC algorithms, and engage vendors to avoid rushed last-minute transitions.
Are PQC algorithms secure today?
Yes, they have undergone years of rigorous evaluation, though cryptography is an evolving field.