Technique to Encode Secret Messages Using the Laws of Motion: Quantum cryptography is revolutionizing the way we encode secret messages, using the very laws of physics—specifically, the laws of quantum mechanics and motion—to make communication more secure than ever before. Imagine sending a message that not even the world’s most powerful computer could crack, all thanks to the strange and wonderful rules that govern the tiniest particles in our universe. This is no longer science fiction; physicists are making it a reality today.

Quantum cryptography, and the techniques developed from it, are not just for scientists in labs. They have the potential to change how we protect our personal data, how banks keep our money safe, and how governments prevent cyberattacks. In this article, we’ll break down how these new methods work, why they matter, and what you need to know to stay ahead in a world where information is everything.
Technique to Encode Secret Messages Using the Laws of Motion
| Feature/Topic | Details & Stats |
|---|---|
| Main Principle | Uses quantum mechanics (laws of motion at the smallest scale) to encrypt and transmit data securely |
| Unbreakable Security | Eavesdropping attempts disturb the system, revealing any intrusion |
| Quantum Key Distribution (QKD) | Securely shares encryption keys using quantum states; proven over 550 km of optical fiber |
| Threat to Classical Encryption | Quantum computers can break RSA-2048 encryption in hours; quantum-safe cryptography is needed |
| Commercial Readiness | QKD is being tested and standardized; full quantum encryption is still in development |
| Official Resource | See NIST Quantum Cryptography for more information |
Quantum cryptography is changing the world of secret messages, using the laws of motion and quantum mechanics to create security that’s practically unbreakable. From banks and hospitals to governments and everyday internet users, this technology promises a future where our information is protected by the very fabric of nature. While some aspects are still in development, the race is on to make quantum-safe communication a reality for everyone.
What Is Quantum Cryptography?
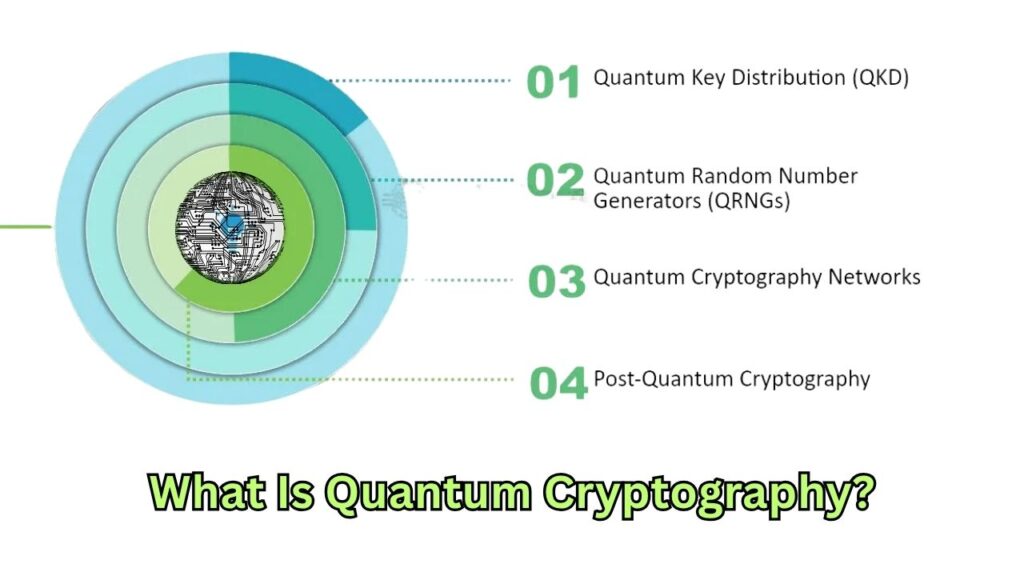
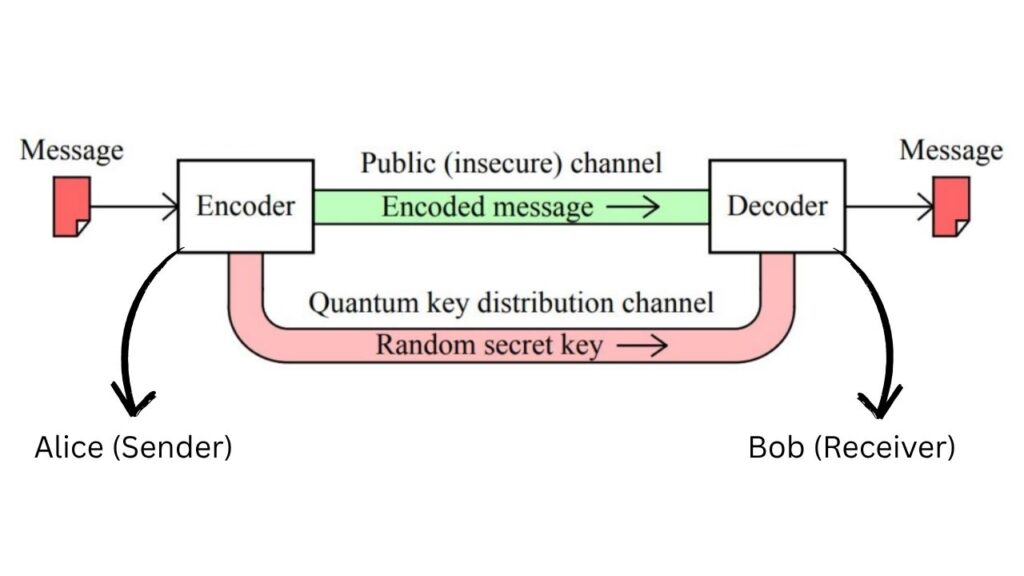
Quantum cryptography is a way of protecting information using the laws of quantum mechanics. Unlike traditional cryptography, which relies on mathematical puzzles, quantum cryptography uses the behavior of tiny particles—like photons—to keep secrets safe. The most famous application is Quantum Key Distribution (QKD), which allows two people to share a secret key that no one else can know, not even if someone is listening in.
Why Is This So Secure?
Here’s the magic: In the quantum world, you can’t look at something without changing it. If a hacker tries to intercept a quantum message, the very act of eavesdropping changes the message itself. This means the sender and receiver will know if someone is trying to snoop, and they can stop the communication before any secrets are stolen.
How Do Physicists Encode Secret Messages Using the Laws of Motion?
1. Quantum Key Distribution (QKD): The Foundation
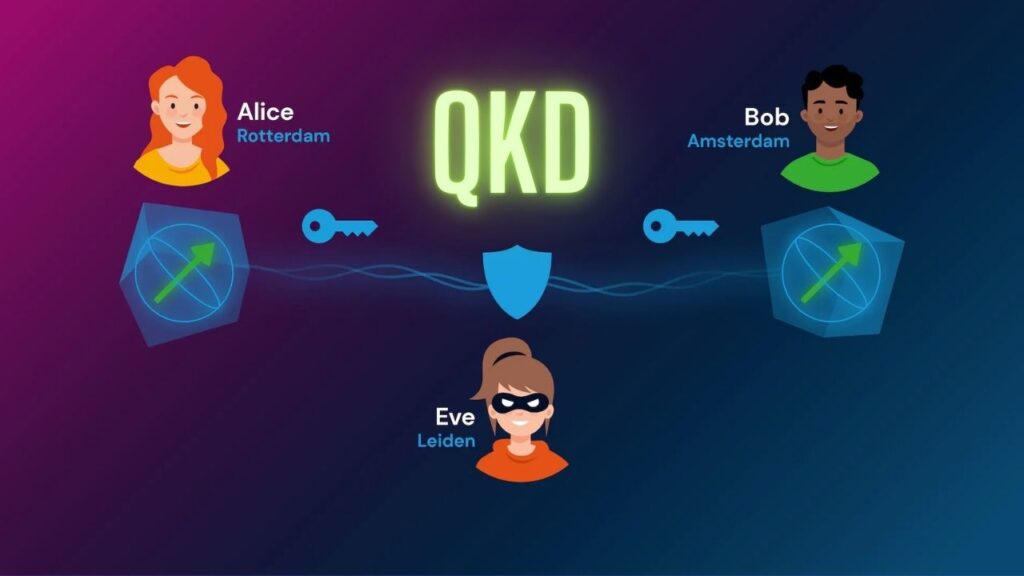
QKD uses photons (particles of light) to send information. Each photon can be in a special state, like spinning up or down, or even both at once (a property called superposition). By sending a series of these photons, two people (commonly called Alice and Bob) can create a secret code, or key.
- If anyone tries to intercept the photons, their state changes, and Alice and Bob will notice.
- Once the key is safely shared, Alice and Bob use it to encrypt and decrypt their messages, just like a secret password.
Real-World Example
Imagine you and your friend each have a box of colored marbles. You agree in advance that red means “yes” and blue means “no.” You send marbles one at a time, and if someone tries to peek at the color on the way, the marble changes color. You’ll know right away if your secret code is safe or not!
2. Quantum Encryption: The Next Level
While QKD protects the key, quantum encryption aims to protect the message itself. This is much harder, but researchers are making progress. One approach is the Kak protocol, which works like a digital version of putting two locks on a box:
- Alice locks the message and sends it to Bob.
- Bob adds his own lock and sends it back.
- Alice removes her lock and sends it to Bob again.
- Bob removes his lock and reads the message.
In the quantum version, these locks are special quantum operations that can’t be copied or measured without destroying the message.
Why Does This Matter? (And Who Should Care?)
For Kids and Curious Minds
This technology means your secrets—like your online chats, your school records, or your favorite game passwords—could one day be protected by the laws of nature themselves. It’s like having an invisible force field around your information!
For Professionals and Businesses
Quantum cryptography is a game-changer for:
- Banks and Financial Institutions: Protecting transactions from cybercriminals.
- Healthcare: Keeping patient data private.
- Government and Defense: Securing communications against espionage.
- Cloud Computing: Ensuring data processed in the cloud stays confidential, even from the cloud provider.
The Science Behind the Security
Quantum Principles at Work
- Superposition: A quantum particle can be in multiple states at once, making it hard to predict or copy.
- Entanglement: Two particles can be linked so that changing one instantly changes the other, no matter how far apart they are.
- No-Cloning Theorem: You can’t make an exact copy of an unknown quantum state.
- Measurement Disturbs the System: Observing a quantum state changes it, revealing eavesdropping attempts.
Quantum Computers: Friend and Foe
Quantum computers can solve certain problems much faster than regular computers. For example, they could break popular encryption methods like RSA, which is used to protect most internet traffic today. That’s why quantum cryptography is so important—it’s the only way to stay ahead of hackers with quantum computers.
Step-by-Step Guide: How Quantum Cryptography Works
Step 1: Prepare the Quantum States
- Alice prepares photons in random quantum states (like different polarizations).
Step 2: Send the Photons
- Alice sends the photons to Bob through a fiber optic cable or even through the air.
Step 3: Measure and Compare
- Bob measures the photons using random settings.
- Alice and Bob publicly compare some of their results (but not all) to check for eavesdropping.
Step 4: Generate the Secret Key
- If the results match, they use the remaining data to create a secret key.
- If not, they know someone tried to listen in, and they discard the key.
Step 5: Encrypt and Send Messages
- Alice and Bob use their secret key to encrypt and decrypt their actual messages using traditional encryption methods.
Practical Advice: Getting Ready for the Quantum Future
- Stay Informed: Follow updates from trusted organizations like NIST Quantum Cryptography.
- Plan for Quantum-Safe Security: Businesses should start evaluating quantum-safe cryptography solutions now, before quantum computers become mainstream.
- Invest in Education: Encourage young learners to explore quantum physics and computer science. The future needs quantum-literate professionals!
Google Research Warns Quantum Computing Could Crack Bitcoin Encryption Sooner Than Expected
Quantum Sensors Now Deliver Unmatched Precision For Medical And Aerospace Breakthroughs
Ultralight 3D-Printed Antennas Cut Weight By 94 Percent With Breakthrough Multi-Material Design
FAQs About Technique to Encode Secret Messages Using the Laws of Motion
Q1: Is quantum cryptography available today?
A: Quantum Key Distribution is already being tested and used in some industries, but full quantum encryption is still in development and not yet widely available.
Q2: Can quantum cryptography be hacked?
A: In theory, no. The laws of quantum mechanics mean any attempt to intercept the message changes it, alerting the sender and receiver.
Q3: Will quantum computers break all current encryption?
A: Powerful quantum computers could break many current encryption methods. That’s why quantum-safe and quantum cryptography are so important for the future.
Q4: How far can quantum messages be sent?
A: Recent advances have enabled secure quantum key distribution over 550 kilometers of optical fiber.