Quantum scientists have developed an entirely new kind of mathematical foundation that could revolutionize how we protect sensitive information in the digital world. This breakthrough isn’t just academic theory — it has the potential to reshape everything from online banking and private messaging to national defense systems. As quantum computers grow closer to reality, this new math may become the bedrock of post-quantum cryptography, ensuring our secrets stay safe even in a future dominated by powerful quantum machines.

Whether you’re a technology professional, a business leader, or just curious about the future of security, this article will help you understand what’s happening, why it matters, and what practical steps you can take to prepare.
Table of Contents
Quantum Scientists Just Built a Whole New Kind of Math
| Topic | Details | Data & Stats | Career & Professional Insights | Official Source |
|---|---|---|---|---|
| Quantum Cryptography Breakthrough | New crypto-math based on quantum one-way state generators and quantum puzzles | Quantum key distribution speeds hitting 1 Tb/s over 100 km fiber | Increased demand for quantum-safe cryptography skills | NIST Post-Quantum Cryptography Project |
The creation of a whole new kind of quantum math marks a critical milestone in cybersecurity. As quantum computers threaten the foundations of classical cryptography, this groundbreaking approach leverages the principles of quantum physics to build encryption that even quantum computers can’t easily break. The future of digital security depends on understanding and embracing these innovations today. Preparing with quantum-safe protocols and education is the best defense in this rapidly approaching era.
What Is the Quantum Cryptography Breakthrough?
The Challenge: Quantum Computers vs. Current Encryption
Currently, most digital security relies on mathematical problems that classical computers find extremely hard to solve. These include things like factoring huge numbers or solving certain algebraic structures. For decades, these problems have kept our communications, finances, and private data secure. However, quantum computers are poised to change that landscape.
Quantum computers use quantum bits, or qubits, which can exist in multiple states simultaneously due to a property called superposition.
This ability, along with entanglement, lets quantum computers perform certain calculations far faster than any classical computer. A famous example is Shor’s algorithm, which quantum computers could use to break widely used encryption methods such as RSA and ECC. When quantum computers become powerful and stable enough, they can unravel these cryptographic locks in minutes or even seconds.
The Scientific Breakthrough
In 2025, teams of quantum scientists introduced a fundamentally new way to build cryptographic systems based on quantum physics itself rather than on classical hard math problems. Instead of relying solely on problems like factoring, the new approach harnesses physical principles inherent in quantum states.
Key Concepts:
- Quantum One-Way State Generators: These are special processes that produce quantum states (made of qubits) that are easy to generate but extraordinarily difficult to reverse-engineer or “unlock” because of the laws of quantum physics.
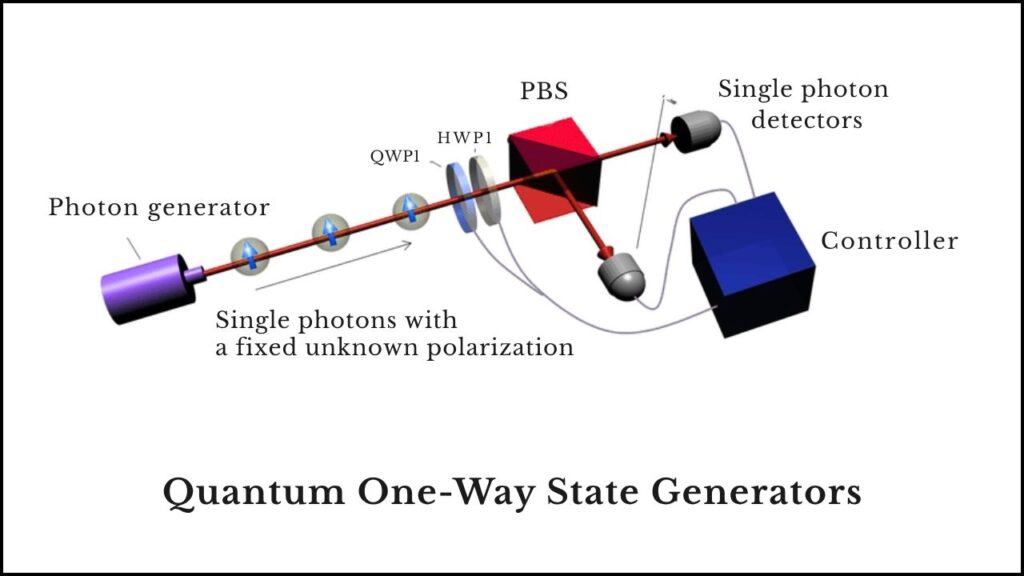
- One-Way Quantum Puzzles: Innovative mathematical puzzles that use quantum information to create locks that cannot be feasibly solved by quantum or classical computers without the correct key. These puzzles enable building secure cryptographic protocols even if traditional math problems become easy for quantum machines.
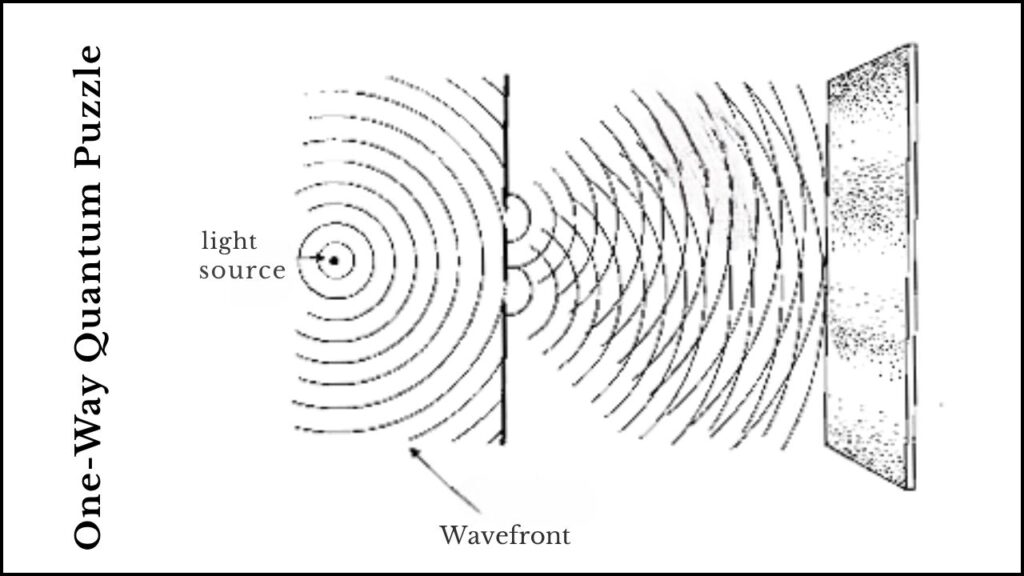
This breakthrough means cryptography can remain secure even in a world where quantum computers can solve all classical hard problems. The security is anchored in the physics of quantum states rather than just computational difficulty.
How Quantum Cryptography Works — A Simple Explanation
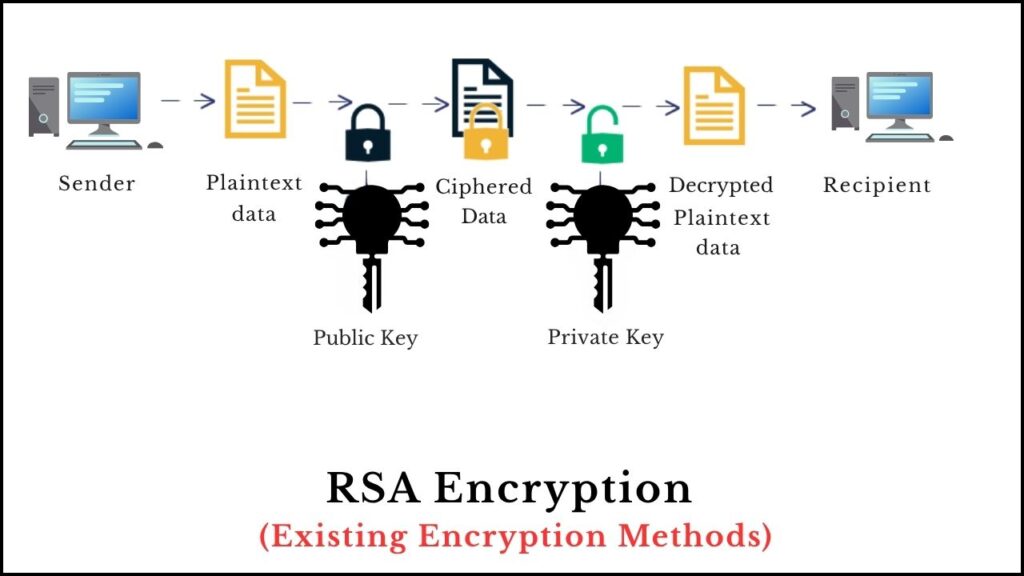
1. The Fragility of Modern Encryption
Today’s encryption depends on tasks that classical computers struggle to do. For example, RSA encryption secures your online banking by relying on the difficulty of factoring enormous numbers. But quantum computers can use the super-powerful Shor’s algorithm to factor these numbers quickly, rendering RSA ineffective.
2. Quantum Key Distribution (QKD) — The First Quantum Solution
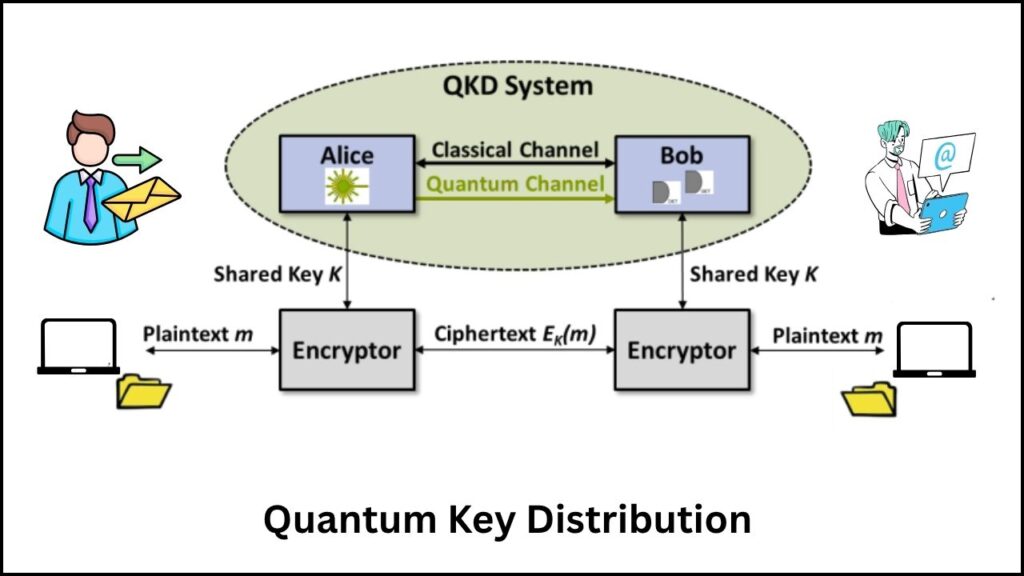
Quantum key distribution uses qubits to share encryption keys securely. Here’s why QKD is special:
- If an eavesdropper tries to intercept the qubits during transmission, the quantum information changes — alerting both sender and receiver to the intrusion.
- This guarantees tamper-evident communication, a security promise impossible with classical keys.
In early 2025, researchers set a new record for QKD speed: distributing encryption keys at 1 terabit per second over 100 kilometers of optical fiber, fast and far enough to protect whole city-wide networks.
3. Moving Beyond QKD: The New Quantum Math
While QKD is effective for sharing keys, the new quantum mathematics allow for many more complex cryptographic tasks such as:
- Creating quantum-proof digital signatures (verifying identities)
- Performing secure multi-party computations (collaborating without exposing private data)
- Implementing advanced zero-knowledge proofs (proving you know something without revealing the secret itself)
In essence, these innovations transform what’s possible in secure communication far beyond current limits.
4. Imagine a Quantum Lockbox
- Traditional locks are based on classical math puzzles that can be cracked with enough computing power.
- Quantum lockboxes rely on state changes governed by the laws of quantum physics. If tampered with, the quantum lock changes state, alerting owners to intrusion attempts instantly.
Why Does This Matter Now?
The Quantum Threat Timeline
Experts estimate that by 2030, around 50–70% of existing encryption methods could be vulnerable to quantum attacks. If businesses or governments don’t prepare, sensitive data—from medical records to national secrets—could be exposed.
A related risk is the so-called “store now, decrypt later” attack, where adversaries capture encrypted data today and wait years until they have quantum computers powerful enough to decrypt it.
Who is at Risk?
- Financial institutions
- Healthcare providers
- National security agencies
- Critical infrastructure operators
All must urgently start adopting quantum-safe technologies to avoid catastrophic breaches.
Are Businesses Ready?
Surveys show less than 15% of organizations have begun preparing for this transition. Awareness and understanding lag behind the rapid pace of quantum advancements, creating a critical window for action.
Practical Guide: How to Prepare for Post-Quantum Cryptography
1. Understand the Risks and Urgency
Recognize that data encrypted today could become vulnerable in a decade or less. This is especially critical for information requiring long-term confidentiality.
2. Audit Your Current Cryptographic Systems
Identify where classical algorithms like RSA, ECC, or Diffie-Hellman are in use, especially for sensitive data or regulated environments.
3. Explore and Adopt Quantum-Resistant Algorithms
Look into algorithms recommended by official bodies such as NIST, which include lattice-based, hash-based, and code-based schemes proven to resist quantum attacks.
4. Pilot Quantum Key Distribution
For ultra-sensitive communications, QKD hardware is increasingly available. Testing and deploying these systems will future-proof your most critical data links.
5. Invest in Skills Development
Train your cybersecurity, software, and IT teams in quantum cryptography basics and quantum risk management. Many tech companies provide quantum education pathways and training programs.
6. Stay Informed and Agile
Keep up with evolving standards and best practices from official sources, and build flexibility into your security infrastructure to adapt quickly as quantum technology advances.
Breakthrough Fixes Quantum Battery Self-Discharge — A Big Step Toward Infinite Power?
New Quantum Theory Just Expanded What We Can Actually Measure
Metasurfaces Could Be the Future of Quantum Computing—Here’s Why Everyone’s Talking
FAQs About Quantum Scientists Just Built a Whole New Kind of Math
Q1. Can quantum computers already hack my data?
Not yet. Current quantum computers are not large or stable enough. The risk lies in the near future—quantum-safe preparations should start now.
Q2. What is “store now, decrypt later”?
Attackers save your encrypted messages today and wait until they have quantum resources to decrypt them years from now. This is why immediate action matters.
Q3. Is quantum cryptography for everyone?
Basic quantum key distribution is commercially available, mostly for enterprise and government use. Widespread adoption is still developing, but quantum-safe encryption migration is underway.
Q4. What can individuals do today?
Use updated, trusted software, practice good password hygiene, and inquire whether your providers are preparing for post-quantum security.
Q5. How can professionals learn more?
Seek out government resources, industry reports, and training from major tech companies like Microsoft and IBM.