China Unveils Quantum-Proof Blockchain Tech: China unveils quantum-proof blockchain tech designed to survive the next cyber era—this headline isn’t just a glimpse into the future, it’s a wake-up call for the present. As the world stands on the brink of a quantum computing revolution, China’s latest breakthrough in blockchain and cryptography is setting new standards for digital security. But what does this mean for you, your business, and the world at large? Let’s break it down in a way that’s easy to understand, yet rich with valuable insights for professionals.

Table of Contents
China Unveils Quantum-Proof Blockchain Tech
| Feature/Fact | Details |
|---|---|
| Quantum-Proof Blockchain | China has developed new blockchain storage technology (EQAS) that resists quantum computer attacks. |
| Quantum-Hybrid Cryptography | First commercial system combining Quantum Key Distribution (QKD) and Post-Quantum Cryptography (PQC). |
| Major Milestone | First quantum-encrypted voice call over 1,000 km between Beijing and Hefei. |
| Quantum Computer | Tianyan-504, a 504-qubit superconducting quantum computer, is operational and cloud-accessible. |
| Industry Impact | Over 500 government agencies and 380 public enterprises protected by China’s quantum network. |
China’s unveiling of quantum-proof blockchain technology marks a turning point in the world of cybersecurity. By combining revolutionary cryptographic methods and a robust quantum network, China is setting a new benchmark for protecting digital data against the next generation of cyber threats. Whether you’re an individual, a business leader, or a government official, now is the time to start preparing for the quantum era. The future of digital security depends on it.
Understanding the Quantum Threat
What Is a Quantum Computer?
A quantum computer is a special kind of computer that uses the principles of quantum physics to solve problems much faster than any traditional computer. While a classic computer uses bits (0s and 1s), a quantum computer uses qubits, which can represent both 0 and 1 at the same time. This allows them to process complex calculations at speeds that were once thought impossible.
Why Are Quantum Computers a Security Risk?
Most of today’s digital security is based on mathematical puzzles that are hard for regular computers to solve. For example, your bank’s website uses encryption algorithms like RSA or elliptic curve cryptography to keep your data safe. These algorithms rely on the fact that certain math problems (like factoring huge numbers) would take thousands of years for a normal computer to crack.
But a quantum computer could solve these problems in hours or even minutes. This means that once quantum computers become powerful enough, they could break the codes that keep our online world secure. Experts call the moment when this happens “Q-Day.”
What Is Blockchain, and Why Does It Matter?
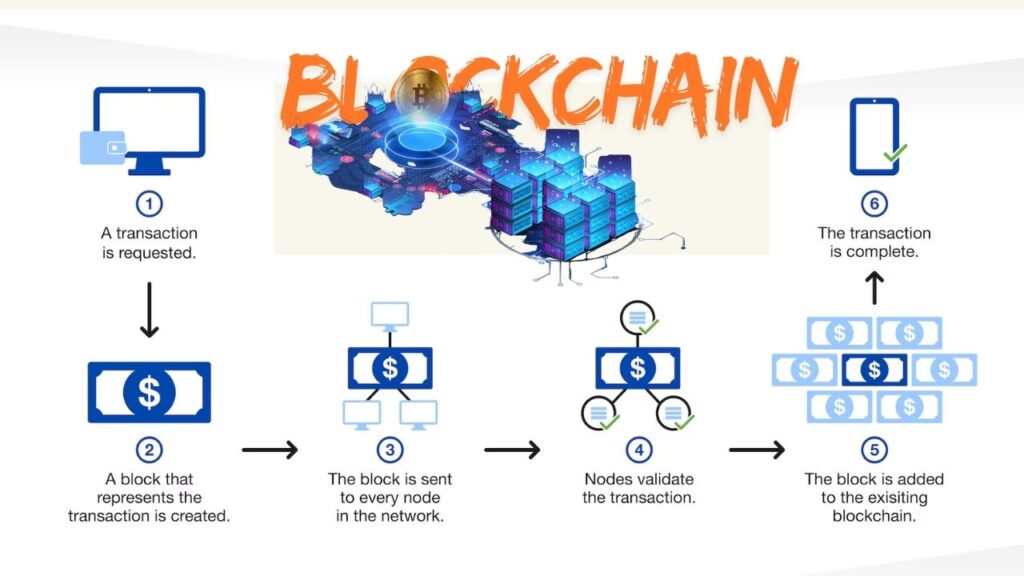
A blockchain is a digital ledger that records transactions in a secure, transparent, and tamper-proof way. It’s the backbone of cryptocurrencies like Bitcoin and Ethereum, but it’s also used in supply chains, healthcare, finance, and government records. The security of blockchain relies on cryptography—if the cryptography is broken, the entire system is at risk.
China’s Quantum-Proof Blockchain: How Does It Work?
1. EQAS: Efficient Quantum-Resistant Authentication Storage
China’s new blockchain storage technology, called EQAS, is designed to withstand attacks from quantum computers. Unlike traditional blockchains that use encryption vulnerable to quantum algorithms, EQAS uses new types of digital signatures and authentication methods that are much harder for quantum computers to break.
Example:
Imagine a lock that’s so advanced, even the world’s best lockpick (a quantum computer) can’t open it. That’s what EQAS aims to be for digital data.
2. Quantum-Hybrid Cryptography System
China Telecom Quantum Group has developed the first commercial cryptography system that combines two cutting-edge technologies:
- Quantum Key Distribution (QKD): This uses the laws of quantum physics to share encryption keys in such a way that any attempt to eavesdrop can be detected immediately. If someone tries to intercept the key, the system knows and can take action.
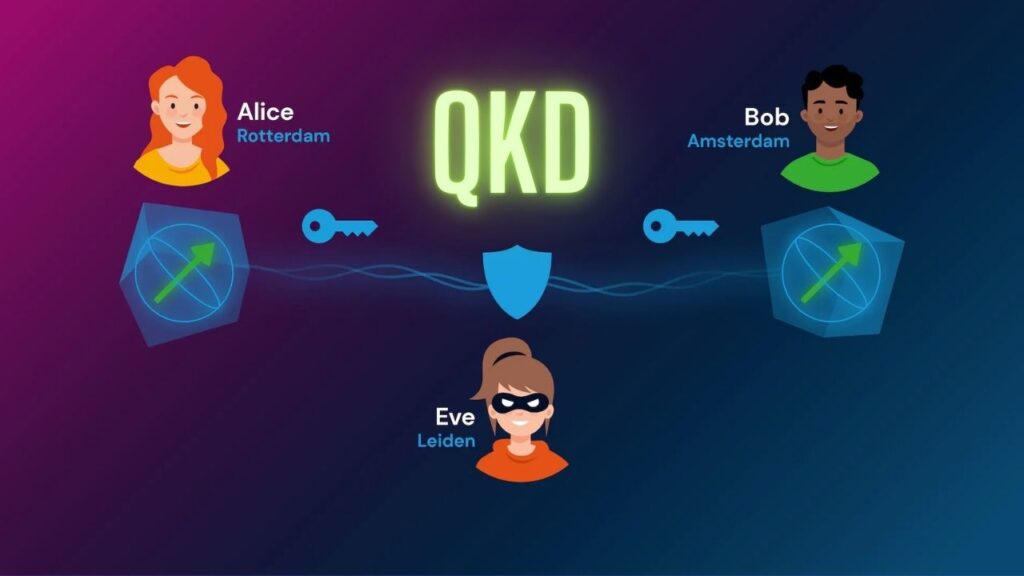
- Post-Quantum Cryptography (PQC): These are new cryptographic algorithms designed to be secure even against quantum computers. They’re based on mathematical problems that are hard for both classical and quantum computers to solve.
This hybrid approach ensures that even if one layer is compromised, the other can still provide protection.
3. Real-World Achievements
China has already demonstrated the power of its quantum-proof technology in the real world. In a landmark achievement, the country completed a quantum-encrypted voice call over a distance of more than 1,000 kilometers between Beijing and Hefei. This call was protected by a national quantum network that already secures the communications of over 500 government agencies and 380 public enterprises.
4. Tianyan-504: China’s Quantum Computing Leap

China’s Tianyan-504 is a 504-qubit superconducting quantum computer. Unlike earlier quantum computers that were mostly experimental, Tianyan-504 is operational and accessible via the cloud. This means researchers and businesses from around the world can use it, accelerating the development and testing of quantum-resistant technologies.
Why Is This a Game-Changer?
For Individuals
- Online Security: Your bank accounts, emails, and personal data are protected against future threats.
- Privacy: Even if hackers use quantum computers, your private messages and records remain safe.
- Trust: You can rely on digital contracts, certificates, and records without fear of tampering.
For Businesses
- Financial Services: Banks and payment providers can continue to offer secure services, even in a quantum-powered world.
- Supply Chains: Companies can track goods and verify transactions with confidence.
- Healthcare: Patient records and sensitive data remain confidential and secure.
For Governments
- National Security: Government communications and classified data are shielded from foreign and domestic cyber threats.
- Public Services: Digital identity, land records, and voting systems can be trusted by citizens.
How Can Organizations Prepare for the Quantum Era?
1. Assess Your Current Security
Start by identifying which systems and applications use encryption that could be vulnerable to quantum attacks. This includes everything from website security (SSL/TLS) to encrypted emails and digital signatures.
2. Upgrade to Post-Quantum Cryptography
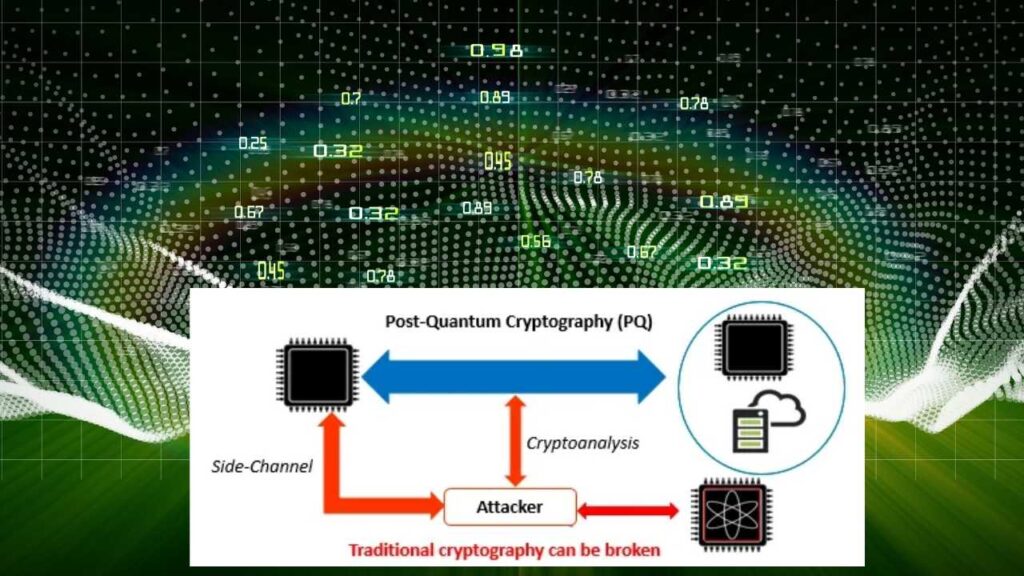
Begin transitioning to post-quantum cryptographic algorithms. These are being developed and standardized by organizations worldwide. Early adoption can help prevent future breaches.
3. Test Quantum-Resistant Solutions
Pilot new technologies like EQAS or quantum-hybrid systems in less critical areas to gain experience and confidence before rolling them out across your organization.
4. Stay Informed and Collaborate
Keep up with developments from national and international standards bodies. Participate in industry groups and collaborate with academic and technology partners to stay ahead of the curve.
5. Train Your Team
Educate your IT and cybersecurity staff about quantum risks and solutions. Provide training on new cryptographic methods and encourage ongoing learning.
Practical Advice for a Quantum-Safe Future
- Start Planning Now: Quantum computers are advancing rapidly. The sooner you start preparing, the better protected you’ll be.
- Don’t Wait for Q-Day: Transitioning to quantum-safe systems takes time. Begin the process before quantum computers become a real threat.
- Work with Trusted Partners: Choose technology providers and consultants who have experience with quantum-resistant solutions.
- Monitor Your Industry: Some sectors, like finance and healthcare, are higher risk and may need to move faster.
- Invest in Research: Support or participate in research initiatives focused on quantum security.
New Quantum Glasses Could Unlock Optimal Error Correction Codes for More Stable Quantum Computers
New Materials Support Progress Toward More Reliable Quantum Computers
Quantum Teleportation Between Computers Achieved for the First Time in History
FAQs About China Unveils Quantum-Proof Blockchain Tech
Q: What is quantum-proof blockchain technology?
A: It’s a new kind of blockchain security that uses advanced cryptography and quantum physics to protect against attacks from quantum computers.
Q: Why are quantum computers a threat to current encryption?
A: Quantum computers can solve the mathematical problems that today’s encryption relies on much faster than traditional computers, making it possible to break codes that were once considered unbreakable.
Q: What is “Q-Day”?
A: “Q-Day” is the term used for the day when quantum computers become powerful enough to break widely used encryption systems.
Q: How is China leading in this field?
A: China has developed operational quantum computers, built a national quantum network, and launched the first commercial quantum-hybrid cryptography system.
Q: What should businesses do now?
A: Assess your current use of encryption, start transitioning to post-quantum cryptography, and stay informed about new standards and technologies.
Q: Will quantum-proof technology be available worldwide?
A: While China is leading, other countries and organizations are also working on quantum-safe technologies. International standards are being developed to ensure global security.