Experts Warn Quantum Cryptography May Not Be Fully Secure Yet: As the world races to defend against the power of quantum computing, one area that’s gaining attention is quantum cryptography—a futuristic method of securing digital communications using quantum mechanics. While it sounds like the ultimate shield, experts are warning that quantum cryptography may not be fully secure yet. Surprised? So were many in the tech world.

Let’s break this down and understand why some of the most advanced forms of encryption still have cracks in their armor—and what businesses, governments, and even average users need to know and do right now.
Experts Warn Quantum Cryptography May Not Be Fully Secure Yet
| Topic | Details |
|---|---|
| What is Quantum Cryptography? | A method of encrypting data using the principles of quantum mechanics, including Quantum Key Distribution (QKD). |
| Current Issue | Experts warn it’s not fully secure or practical yet due to infrastructure, scalability, and implementation flaws. |
| Post-Quantum Cryptography (PQC) | Algorithms resistant to quantum attacks are being developed, but deployment is still limited. |
| Real Risks | Harvest-now, decrypt-later threats, poor readiness across industries, and broken algorithms (e.g., SIKE). |
| Advice for Businesses | Begin migration now, use hybrid encryption, invest in crypto-agility, and stay updated with NIST standards. |
| Authoritative Source | NIST Post-Quantum Cryptography Project |
While quantum cryptography sounds unbreakable, the reality is more nuanced. Experts are waving red flags—not because the science is wrong, but because real-world implementation lags behind the theory. If you think you’re safe just because you’re encrypted, think again.
The race to secure the future starts now, and it’s not just for cybersecurity experts or government agencies. From financial institutions to health care providers to messaging apps, everyone needs to prepare for the coming shift.
What Is Quantum Cryptography?
Quantum cryptography refers to using the bizarre rules of quantum physics to secure digital information. Unlike traditional encryption, which relies on complex math, quantum methods rely on the physical laws of nature—like how photons behave—to create unhackable communication channels.
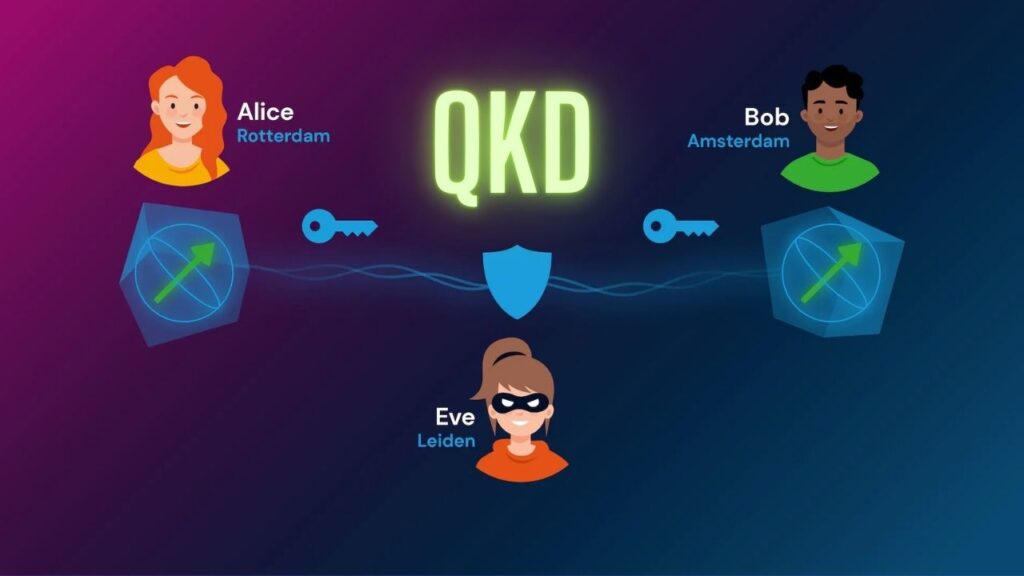
The best-known application is Quantum Key Distribution (QKD). It sends encryption keys using quantum particles. If anyone tries to intercept the key, the particles’ state changes, alerting both sender and receiver.
Sounds cool, right? But in practice, things are messier.
Why Quantum Cryptography Isn’t Fully Secure Yet
1. Real-World Deployments Are Fragile
While QKD is theoretically secure, its practical implementation is fragile. It requires dedicated fiber optics or satellites, which are expensive and limited in reach. And even small environmental factors—like noise or equipment quality—can affect the system.
2. The Post-Quantum Algorithms Are New and Still Evolving
To counteract quantum threats, researchers are also building Post-Quantum Cryptography (PQC)—classical algorithms designed to resist attacks from quantum computers.
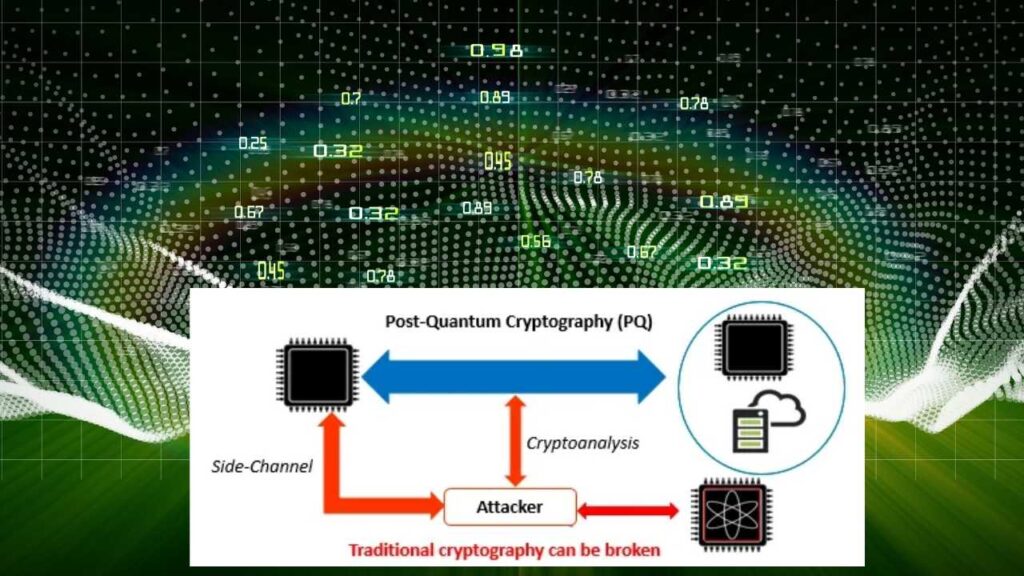
In 2022, the National Institute of Standards and Technology (NIST) selected several finalists for standardization, including Kyber and Dilithium. But even these algorithms are still undergoing real-world testing. In fact, a candidate algorithm called SIKE was broken using traditional computers, proving vulnerabilities still exist.
3. Harvest-Now, Decrypt-Later Is Already Happening
Adversaries—like state-sponsored hackers—may be recording encrypted traffic today. They’ll just wait for quantum computers to mature, then decrypt it all in minutes. This tactic is known as “harvest-now, decrypt-later.”
So even if quantum-safe encryption becomes mainstream in 2030, your secrets from 2025 might already be compromised if you don’t act now.
4. Businesses Aren’t Ready
A recent study showed that many financial and healthcare organizations scored below average in quantum readiness—with a score of just 2.4 out of 5.
Experts from the UK’s National Cyber Security Centre (NCSC) are urging governments and companies to start transitioning now, even if quantum computers aren’t breaking encryption just yet.
What’s the Difference Between PQC and QKD?
| Aspect | Post-Quantum Cryptography | Quantum Key Distribution |
|---|---|---|
| Type | Software-based encryption | Physics-based key exchange |
| Scalability | High (works with existing internet) | Low (needs special fiber or satellite links) |
| Cost | Low to moderate | High |
| Deployment | Already being tested in browsers and apps | Limited to government or elite institutions |
Conclusion: PQC is more practical for widespread use, while QKD is still mainly experimental or for high-security government systems.
A Step-By-Step Guide: How to Prepare for the Quantum Era
Step 1: Understand What You’re Protecting
- Identify sensitive data that must remain secure for 10–20+ years: health records, financial contracts, government documents, etc.
- Ask: “If this got decrypted in 2030, would it matter?”
Step 2: Build Crypto-Agility
- Crypto-agility means your systems can quickly switch encryption algorithms without major overhauls.
- Start by making an inventory of all cryptographic systems in use—TLS, VPNs, encrypted databases, etc.
Step 3: Test Post-Quantum Algorithms in Parallel
- Use hybrid encryption: combine current algorithms (like RSA or ECC) with quantum-resistant ones (like Kyber).
- Example: Messaging apps are beginning to adopt hybrid protocols combining X25519 with Kyber.
Step 4: Stay Updated With Standards
- Monitor updates from organizations like NIST, ETSI, and IETF for official algorithm adoption and deployment guidance.
Step 5: Educate Your Teams
- Train IT, compliance, and cybersecurity teams on the implications of quantum computing.
- Encourage participation in quantum-readiness workshops or vendor pilot programs.
Quantum Mechanics Centennial Spurs International Year Of Quantum Science & Technology
Oxford Physicists Achieve Record-Low Quantum-Bit Error Rate: One In 6.7 Million
FAQs About Experts Warn Quantum Cryptography May Not Be Fully Secure Yet
Is quantum cryptography already being used?
Yes, but mostly in limited settings like national security communications or high-budget experiments. It’s not yet feasible for mass use.
What is the safest encryption right now?
Currently, a hybrid model combining traditional algorithms (like RSA or ECC) with PQC algorithms (like Kyber) is considered safest.
When will quantum computers be able to break encryption?
Estimates vary, but many experts say between 2030 and 2040. Companies like Google, IBM, and several countries are aggressively advancing this timeline.
Will all encryption be useless in the future?
No. Quantum-resistant algorithms are being developed. The challenge is deploying them globally before it’s too late.
How do I know if my company is quantum-safe?
Most aren’t. Start by auditing your cryptographic systems and talk to vendors about their PQC roadmap.