The GPUHammer exploit has sent shockwaves through the worlds of cybersecurity and artificial intelligence. This recently discovered vulnerability specifically targets NVIDIA GPUs, the powerful processors behind much of today’s AI revolution, by exploiting a hardware memory flaw known as Rowhammer. The implications are serious: even a single, tiny change in memory can cause AI models to fail catastrophically, threatening the reliability and security of critical systems.

In this article, we’ll break down what GPUHammer is, why it matters, how it works, and—most importantly—what you can do to protect your AI models and data. Whether you’re a student, a tech professional, or simply curious about the latest in computer security, you’ll find clear explanations, real-world examples, and practical advice to help you stay informed and secure.
Table of Contents
GPUHammer Exploit Targets NVIDIA GPUs
| Feature/Fact | Details & Stats |
|---|---|
| Exploit Name | GPUHammer |
| Target | NVIDIA GPUs (A6000 with GDDR6; others may be at risk) |
| Type of Attack | Rowhammer (memory disturbance via repeated row activation) |
| Impact on AI Models | Accuracy drop from 80% to <1% with a single bit flip |
| Affected Architectures | AlexNet, VGG16, ResNet50, DenseNet161, InceptionV3 (and potentially more) |
| Mitigation | Enable System-Level ECC (Error Correcting Code); default on Hopper/Blackwell GPUs |
| Performance Overhead (with ECC) | 3–10% slower, 6.5% more memory used |
| Industry Response | NVIDIA issued advisory; recommends ECC activation |
| Official Resource | NVIDIA Security Advisory |
The GPUHammer exploit is a landmark discovery in the field of hardware security, exposing a critical vulnerability in NVIDIA GPUs that threatens the integrity of AI models worldwide. By exploiting a memory flaw known as Rowhammer, attackers can cause devastating bit flips that cripple AI systems and break the promise of secure, reliable computing. The best defense is to enable ECC memory protection on all affected GPUs and to remain vigilant about hardware security best practices.
What Is GPUHammer and Why Is It Important?
GPUHammer is a new kind of attack that adapts the well-known Rowhammer technique—originally a threat to standard computer memory—to the specialized memory used in NVIDIA graphics cards. This is a big deal because NVIDIA GPUs are everywhere: in data centers, research labs, cloud platforms, and even some personal computers.
The researchers who discovered GPUHammer showed that by carefully and repeatedly accessing certain rows of memory on an NVIDIA GPU, they could cause tiny electrical disturbances. These disturbances can flip bits in adjacent memory cells, changing the data stored there. While this might sound minor, in the world of AI, even a single bit flip can have dramatic consequences.
For example, in one test, a single bit flip caused an AI model’s accuracy on a standard image recognition task to crash from 80% to less than 1%. This kind of failure could have serious consequences in real-world situations, such as medical diagnosis, autonomous vehicles, financial trading, or security systems.
Understanding Rowhammer: The Memory Flaw Behind GPUHammer
What Is Rowhammer?
Rowhammer is a hardware vulnerability that was first discovered in traditional computer memory (DRAM) over a decade ago. Normally, each memory cell is supposed to be isolated from its neighbors. But Rowhammer exploits a quirk of physics: if you access (or “hammer”) one row of memory over and over very quickly, you can cause electrical interference that flips bits in nearby rows.
Imagine you have a row of dominoes. If you tap one row hard and fast enough, you might accidentally knock over dominoes in the next row, even though you didn’t touch them directly. In the digital world, this means data can be changed without any software bug or malware—just by manipulating how the hardware works.
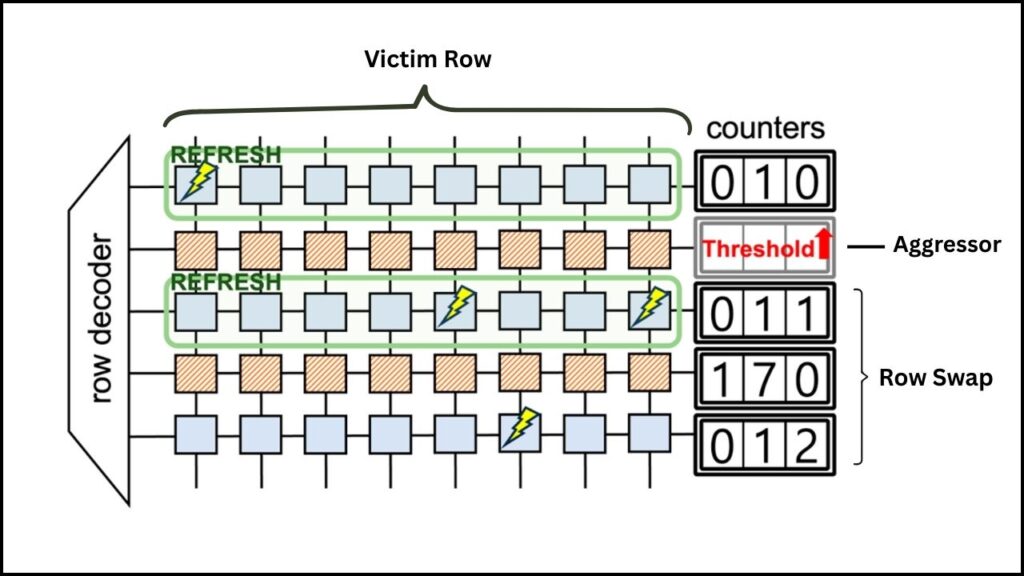
How GPUHammer Brings Rowhammer to GPUs
Until recently, Rowhammer attacks were mostly a problem for CPUs and their memory. GPUs, especially those used for AI and machine learning, use a different kind of memory called GDDR6, which was thought to be more resistant to this kind of attack.
However, researchers from the University of Toronto proved that Rowhammer can be adapted to GPUs. They did this by:
- Reverse-engineering the memory mapping used by NVIDIA GPUs, which is not publicly documented.
- Designing specialized programs that can “hammer” memory rows in parallel, taking advantage of the GPU’s massive computing power.
- Targeting the most significant bit of the exponent in FP16 (half-precision floating point) weights, which are commonly used in modern AI models.
By flipping just one bit in the right place, they could cause AI models to make completely wrong predictions. In their tests, well-known neural networks like AlexNet, VGG16, ResNet50, DenseNet161, and InceptionV3 were all found to be highly vulnerable.
Real-World Impact: How GPUHammer Threatens AI Model Integrity
Why Are AI Models So Sensitive to Bit Flips?
AI models, especially deep neural networks, rely on millions of tiny weights and parameters. These are often stored in half-precision (FP16) format to save memory and speed up calculations. In FP16, the most significant bit of the exponent can dramatically change the value of a weight. If this bit is flipped, a small number can suddenly become extremely large or vice versa, causing the entire model’s predictions to go haywire.
For example, in the researchers’ experiments, flipping a single bit in a model’s memory caused its accuracy on the ImageNet dataset—a standard benchmark for image recognition—to drop from 80% to just 0.1%. This isn’t just a minor error; it’s a total failure.
Broader Risks for Cloud and Multi-Tenant Environments
The risks go beyond just one computer or one user. In cloud environments, GPUs are often shared between multiple customers. If one user can run a GPUHammer attack, they might be able to corrupt or steal data from others using the same hardware. This breaks the fundamental promise of isolation and security in shared computing environments.
For businesses, research institutions, and anyone running sensitive workloads on shared GPUs, this is a serious concern. It means that even if your software is perfectly secure, the hardware itself could be a weak point.
Who Is at Risk from GPUHammer?
Widespread Use of NVIDIA GPUs
NVIDIA dominates the GPU market, especially for AI and high-performance computing. Their GPUs are found in:
- Data centers powering cloud AI services
- Research labs running scientific simulations
- Enterprise servers handling big data analytics
- Personal computers used for gaming, content creation, and more
Because of this, the potential impact of GPUHammer is vast. While the initial research focused on the A6000 model with GDDR6 memory, other models and memory types could also be at risk, depending on their architecture and configuration.
Not Just a Theoretical Threat
Although GPUHammer has so far only been demonstrated in research settings, the technique is now public knowledge. This increases the risk that malicious actors could attempt to use it in real-world attacks, especially in environments where GPUs are shared or used for sensitive tasks.
How Can You Protect Your AI Models and Data?
NVIDIA’s Official Recommendation: Enable ECC
The most effective defense against GPUHammer is to enable System-Level Error Correcting Code (ECC) on your NVIDIA GPUs. ECC works by detecting and correcting single-bit errors in memory before they can cause harm. This is a hardware feature, not a software patch, so it must be activated at the system or firmware level.
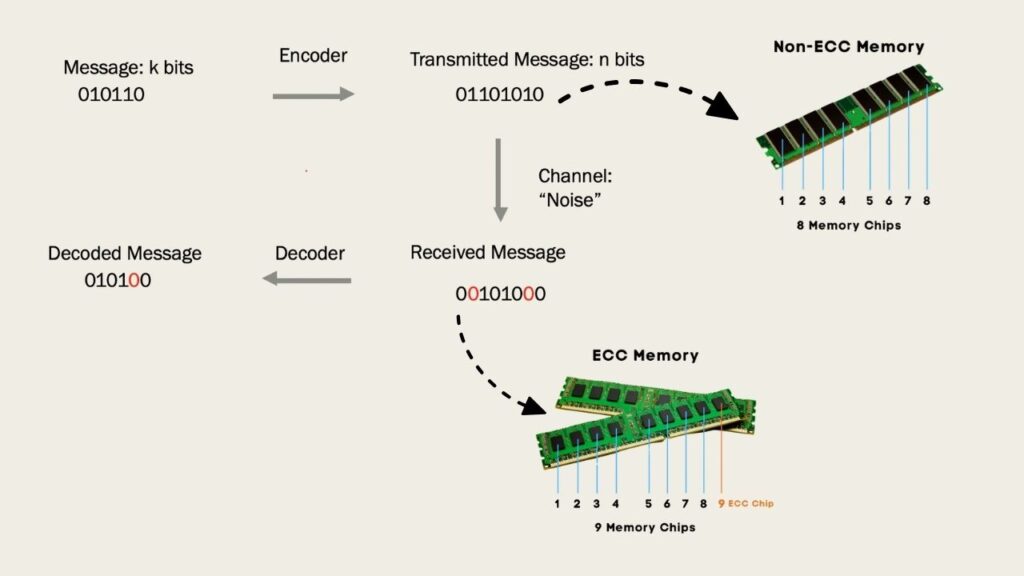
- On newer NVIDIA GPUs (such as Hopper and Blackwell architectures): ECC is enabled by default.
- On older models: You may need to manually enable ECC in your system settings or through the NVIDIA Control Panel.
- Performance impact: Enabling ECC uses about 6.5% more memory and can slow down performance by 3–10%. For most professional and enterprise workloads, this is a small price to pay for greatly improved security.
Step-by-Step: How to Enable ECC on NVIDIA GPUs
- Identify your GPU model: Use the
nvidia-smicommand or check the NVIDIA Control Panel. - Enable ECC: In the NVIDIA Control Panel or via command line (
nvidia-smi -e 1). - Restart your system: Some changes require a reboot to take effect.
- Verify ECC status: Use
nvidia-smi -qto confirm ECC is active.
Best Practices for Cloud and Enterprise Environments
- Contact your cloud provider: Ask if ECC is enabled by default on your GPU instances. Major providers are aware of the issue and may have already taken steps to protect customers.
- Request dedicated GPUs: For the most sensitive workloads, avoid sharing GPUs with other customers.
- Monitor AI model performance: Set up alerts for sudden drops in model accuracy, which could indicate tampering or hardware errors.
- Regularly update your systems: While software updates can’t fix hardware flaws, they can help protect against other vulnerabilities and ensure your system is using the latest security features.
NVIDIA Powers Europe’s Fastest Supercomputer With Game-Changing Grace Hopper Platform
China’s AI Chip War Strategy May Already Be Outpacing the West’s Response
Ooredoo and NVIDIA Unite to Build Qatar’s Supercharged AI Future
FAQs About GPUHammer Exploit Targets NVIDIA GPUs
What is a bit flip, and why does it matter?
A bit flip is when a single binary digit (0 or 1) in computer memory changes unexpectedly. In AI models, even one bit flip in the right place can cause the model to make completely wrong predictions.
Is my gaming PC at risk?
Most home users are unlikely to be targeted by GPUHammer, as the attack requires specialized knowledge and access. The risk is much greater for enterprise, research, and cloud environments where GPUs are shared or used for critical tasks.
Has this attack been used in the wild?
So far, GPUHammer has only been demonstrated by security researchers. However, now that the technique is public, attackers may try to use it in real-world attacks, especially in high-value targets.
Does updating my drivers fix the problem?
No. Rowhammer is a hardware vulnerability, not a software bug. Software updates alone cannot fix it, but enabling ECC can protect against bit flips.
Are AMD or Intel GPUs affected?
This specific attack targets NVIDIA GPUs with GDDR6 memory. However, Rowhammer vulnerabilities have been found in other types of memory and hardware, so ongoing research is needed.
The Bigger Picture: Hardware Security in the Age of AI
The discovery of GPUHammer is a powerful reminder that as we push the boundaries of what computers can do, hardware-level security is just as important as software updates and firewalls. Modern AI models are only as trustworthy as the hardware they run on. If the underlying memory can be tampered with, even the most advanced algorithms can be rendered useless—or worse, dangerous.
For organizations that rely on AI, high-performance computing, or cloud services, this means taking a proactive approach to hardware security:
- Enable ECC on all professional and data center GPUs.
- Work with cloud providers to ensure best practices are followed.
- Stay informed about emerging threats and new security features.