In today’s rapidly evolving digital world, cybersecurity faces unprecedented challenges, especially with the rise of quantum computing. Enter Naoris Protocol, a pioneering decentralized cybersecurity network that recently launched its native token, $NAORIS, explicitly designed to resist the immense computational power of quantum computers. This groundbreaking development promises to safeguard the future of Web3, traditional Internet systems, IoT devices, and critical industries like finance and defense.

Table of Contents
What Is Naoris Protocol and Why Does It Matter?
Naoris Protocol builds a quantum-resistant security layer for blockchain and digital infrastructure by using post-quantum cryptographic algorithms that are officially validated by the National Institute of Standards and Technology (NIST), such as Dilithium-5 and Key Encapsulation Mechanisms (KEMs). These algorithms rely on mathematical problems that even the most advanced quantum computers cannot solve efficiently today, making digital transactions and communications inherently secure against quantum attacks.
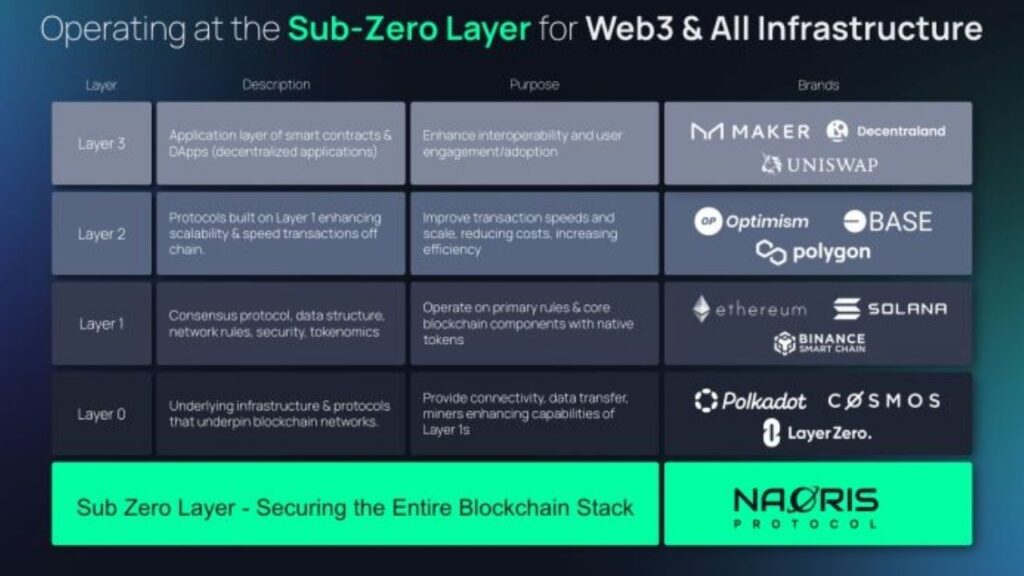
Unlike traditional blockchain security methods like RSA or ECDSA—which quantum computers threaten to break—Naoris introduces a novel Sub-Zero Layer: a foundational security protocol operating beneath standard blockchain layers (Layer 0 to Layer 3). This layer integrates seamlessly with any EVM-compatible blockchain without requiring disruptive upgrades or hard forks, providing scalable, real-time quantum-safe protection.
Naoris Protocol Just Launched a Token That Quantum Computers Can’t Crack
| Feature | Detail |
|---|---|
| $NAORIS Token Launch Date | July 31, 2025 |
| Initial Circulating Supply | 599.26 million tokens |
| Fully Diluted Valuation | $500 million |
| Transactions Processed | Over 98 million quantum-resistant transactions on testnet |
| Wallets Onboarded | 3.3 million wallets |
| Security Nodes Activated | 1 million+ devices functioning as decentralized validators |
| Cyber Threats Mitigated | Approximately 461 million cyber threats blocked |
| Consensus Mechanism | Decentralized Proof of Security (dPoSec) |
| AI-Powered Security | Swarm AI detects and neutralizes threats in real-time |
| Tokenomics | 1 billion total tokens; 35% reserved for staking rewards, 30% treasury & partnerships, 4% public sale |
| Supported Exchanges | Binance Alpha, MEXC, Bitget, Gate.io, ZBX, and more |
| Institutional Backing | Draper Associates, IBM collaborations, Mason Labs, and others |
| Official Website | naorisprotocol.com |
With the official launch of the $NAORIS token, Naoris Protocol is revolutionizing cybersecurity by delivering a scalable, decentralized, and quantum-resistant security framework tailor-made for the digital future. By combining state-of-the-art post-quantum cryptography, decentralized consensus through dPoSec, and AI-powered threat detection, Naoris Protocol is paving the way for safer Web3 applications, enterprise systems, and critical infrastructure. Staying ahead of the quantum threat curve not only protects digital assets today but also builds trust and resilience for the blockchain ecosystems of tomorrow.
How Naoris Protocol Works: A Step-By-Step Guide
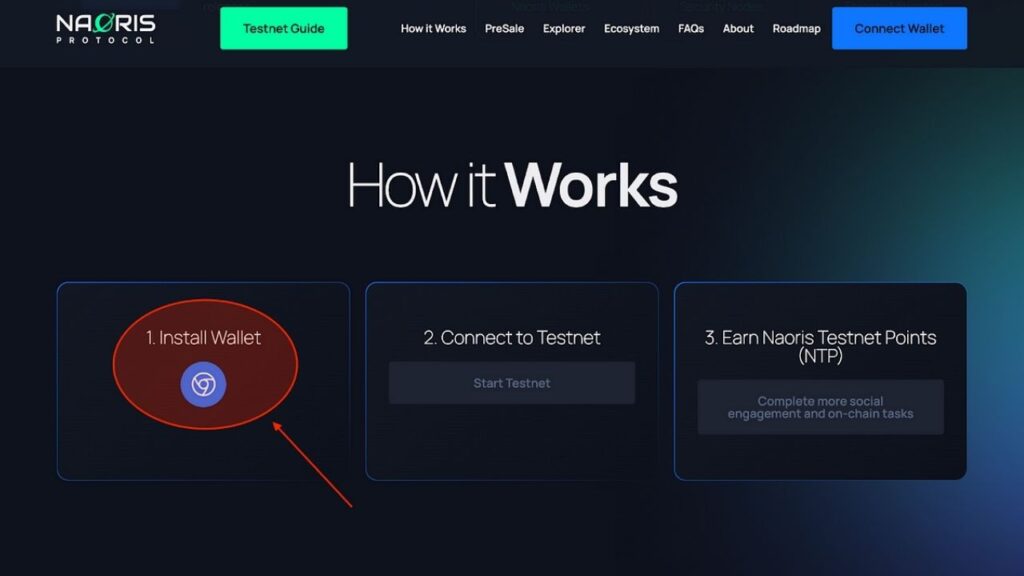
1. The Sub-Zero Layer – A Quantum-Resistant Foundation
Naoris Protocol’s Sub-Zero Layer acts as an invisible but powerful shield operating beneath existing blockchain networks. Unlike solutions that require rebuilding or downtime, this layer integrates smoothly with current EVM-compatible blockchains, enhancing security without disrupting operations or requiring system migrations.
2. Cutting-Edge Post-Quantum Cryptography
At the core of the protocol are post-quantum algorithms like Dilithium-5 and KEMs, vetted by NIST. These cryptographic standards use difficult mathematical challenges believed to be resistant to quantum decryption methods. They protect the creation, validation, and transmission of cryptographic keys essential for blockchain security and identity verification.
3. Decentralized Proof of Security (dPoSec)
Naoris replaces traditional blockchain consensus mechanisms with dPoSec, which distributes security validation across millions of devices globally. Each participating device operates as an autonomous security node, collectively forming a decentralized mesh network that is far more resilient to attacks than centralized systems.
4. Swarm AI: Smarter, Real-Time Threat Detection
The protocol integrates Swarm AI, an artificial intelligence system designed to continuously analyze network data across validator nodes. This collaborative AI system detects new and evolving cyber threats early, isolates dangers, and neutralizes attacks automatically—offering a faster, smarter, and decentralized defense system compared to traditional cybersecurity approaches.
5. Role of the $NAORIS Token and Economic Design
The native $NAORIS token is the lifeblood of the network. It incentivizes participation by:
- Facilitating staking to secure and validate transactions.
- Rewarding node operators and contributors who protect network integrity.
- Enabling governance functions and access to advanced security services like anomaly detection and smart contract audits.
With a total supply of 1 billion tokens, the allocation strikes a balance between rewards (35%), long-term development & partnerships (30%), and initial public availability (4%), ensuring sustainable growth and community engagement.
Why Is Quantum Resistance Crucial?
Quantum computers represent a leap in processing power that threatens to render current widely used encryption methods obsolete. Algorithms such as RSA and ECDSA cannot withstand attacks by quantum computers running algorithms like Shor’s algorithm, which can break these traditional encryptions and potentially expose private keys and sensitive data.
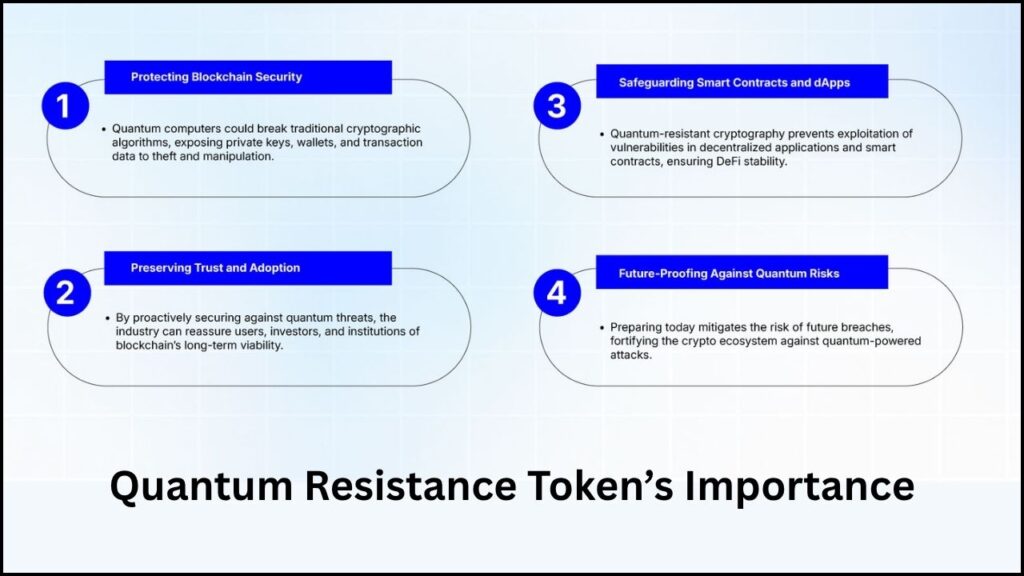
Because of this looming threat, national and international institutions, including NIST, NATO, and ETSI, are actively standardizing quantum-resistant cryptographic methods. Global experts expect widespread migration to these new post-quantum standards by the end of this decade. Naoris Protocol is ahead of the curve, securing not only future blockchain infrastructure but also the broader digital ecosystem today.
Real-World Impact and Industry Adoption
After launching its post-quantum testnet in early 2025, Naoris Protocol has proven its capability with:
- Over 98 million quantum-secure transactions processed
- 3.3 million wallets created
- 1 million+ security nodes deployed
- Approximately 461 million cyber threats neutralized
- Active pilots in finance, defense, telecommunications, and energy sectors
With heavyweight investors like Draper Associates and strategic tech collaborations with companies such as IBM, Naoris is rapidly establishing itself as a critical component of the future decentralized infrastructure, protecting vital systems against the next generation of security challenges.
Practical Advice: How You Can Benefit from Naoris Protocol
Whether you’re a developer, IT manager, investor, or cybersecurity professional, here’s how you can use Naoris Protocol:
- Developers: Seamlessly integrate Naoris’s Sub-Zero Layer into your EVM-compatible blockchain without downtime or complex updates.
- Enterprises: Leverage decentralized security validation to protect sensitive data and maintain compliance against sophisticated cyber threats.
- Investors: Engage with a promising ecosystem by acquiring $NAORIS tokens and participating in staking for rewards.
- IoT Operators and Critical Infrastructure Managers: Protect vast networks of devices with Naoris’s AI-driven, decentralized threat detection and automated response.
Quantum Scientists Just Built a Whole New Kind of Math — And It Could Rewrite Cryptography
Experts Warn Quantum Cryptography May Not Be Fully Secure Yet
FAQs About Naoris Protocol Just Launched a Token That Quantum Computers Can’t Crack
What is post-quantum cryptography?
It refers to cryptographic algorithms specifically designed to resist attacks from quantum computers, ensuring long-term security even as computing power grows.
How does the Sub-Zero Layer protect blockchain transactions?
The Sub-Zero Layer operates beneath existing blockchain layers, adding a quantum-resistant shield to transactions without needing to alter or restart current systems.
What is Decentralized Proof of Security (dPoSec)?
It’s a consensus mechanism that converts every connected device into an autonomous security validator, distributing trust and network safety across many nodes instead of relying on a central authority.
When will $NAORIS be publicly tradable?
$NAORIS became available for public trading on July 31, 2025, across major exchanges including Binance Alpha, MEXC, Bitget, Gate.io, and ZBX.
How can someone participate in Naoris Protocol?
You can buy $NAORIS tokens from participating exchanges, stake tokens to support network security, and integrate Naoris’s protocols into blockchain applications or enterprise systems.